keychat on Nostr: A ratchet can only turn in one direction. The double ratchet means two types of ...
A ratchet can only turn in one direction.
The double ratchet means two types of ratchets: a KDF ratchet (the small ratchet in the diagram) and a DH ratchet (the large ratchet in the diagram).
KDF stands for Key Derivation Function. A hash function is the simplest KDF because it is one-way. K1=hash(K0), K2=hash(K1), K3=hash(K2), K4=hash(K3)... K1 is used to encrypt the first message, K2 to encrypt the second message, and so on. Once used, the key is deleted. If an attacker obtains the latest encryption key K5, they cannot reverse-engineer K4, K3, K2, or K1, ensuring the security of historical messages. Thus, the KDF provides forward secrecy to the encryption protocol.
However, the attacker can derive K6, K7, K8..., which means there is no backward secrecy. This is where the DH ratchet comes into play.
The Diffie–Hellman (DH) key exchange is a mathematical method for securely exchanging cryptographic keys over a public channel. Alice, using her private key S1 and Bob’s public key P2, can compute a value. Similarly, Bob, using his private key S2 and Alice’s public key P1, can compute a value. These two values are equal.
Alice and Bob continuously generate new DH key pairs for new messages on the client side and attach the public key in plaintext to the message. The message recipient can then use this public key and their private key to perform the DH computation. This DH ratchet effectively resets the KDF ratchet with the DH ratchet. Because the attacker does not know the latest DH private key, they cannot derive future encryption keys, thus providing backward secrecy.
Therefore, in the double ratchet algorithm, the KDF ratchet ensures forward secrecy, and the DH ratchet ensures backward secrecy, together achieving both forward and backward secrecy.
We recommend the following video, which provides a more intuitive animation demonstration.
https://youtu.be/9sO2qdTci-s?si=BXLU33BRANWAJKMz
https://youtu.be/7uEeE3TUqmU?si=jpPOR_O61IppgJxl
(We hope users can understand the basic principles to judge for themselves which chat applications are good.)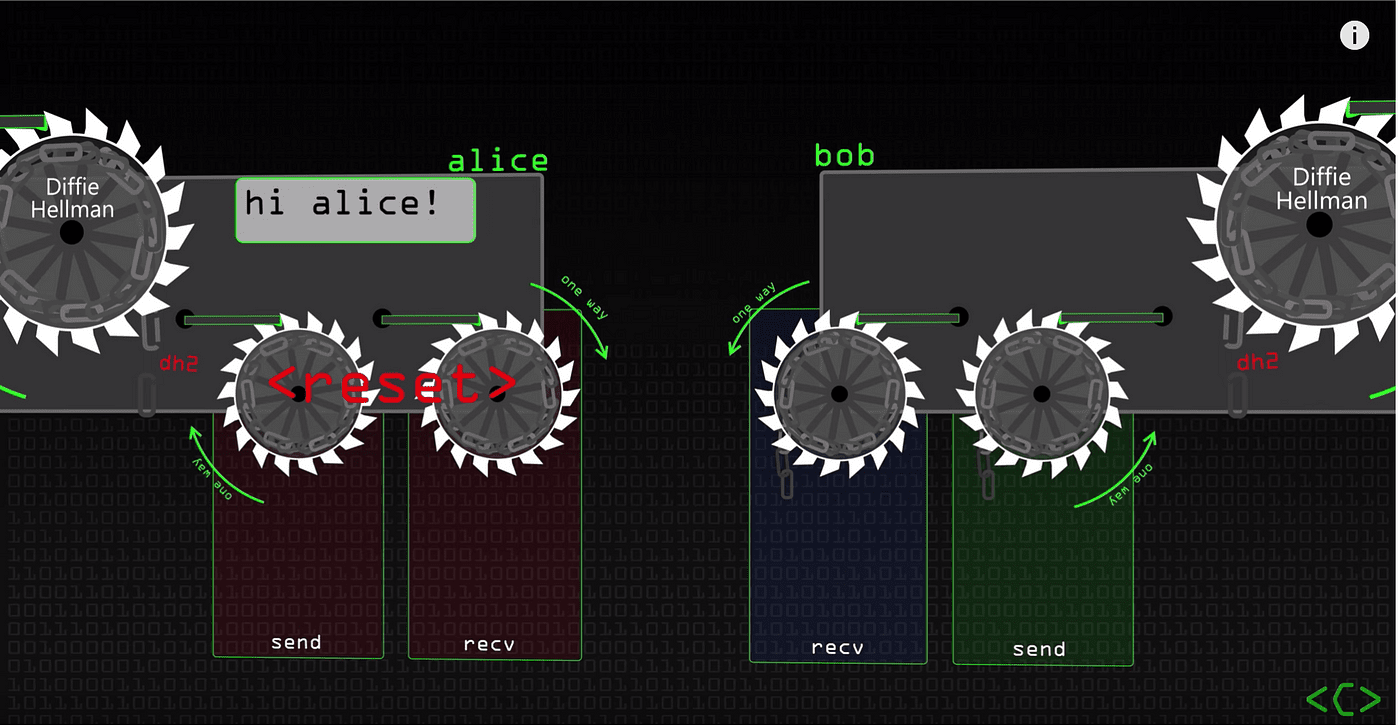
The double ratchet means two types of ratchets: a KDF ratchet (the small ratchet in the diagram) and a DH ratchet (the large ratchet in the diagram).
KDF stands for Key Derivation Function. A hash function is the simplest KDF because it is one-way. K1=hash(K0), K2=hash(K1), K3=hash(K2), K4=hash(K3)... K1 is used to encrypt the first message, K2 to encrypt the second message, and so on. Once used, the key is deleted. If an attacker obtains the latest encryption key K5, they cannot reverse-engineer K4, K3, K2, or K1, ensuring the security of historical messages. Thus, the KDF provides forward secrecy to the encryption protocol.
However, the attacker can derive K6, K7, K8..., which means there is no backward secrecy. This is where the DH ratchet comes into play.
The Diffie–Hellman (DH) key exchange is a mathematical method for securely exchanging cryptographic keys over a public channel. Alice, using her private key S1 and Bob’s public key P2, can compute a value. Similarly, Bob, using his private key S2 and Alice’s public key P1, can compute a value. These two values are equal.
Alice and Bob continuously generate new DH key pairs for new messages on the client side and attach the public key in plaintext to the message. The message recipient can then use this public key and their private key to perform the DH computation. This DH ratchet effectively resets the KDF ratchet with the DH ratchet. Because the attacker does not know the latest DH private key, they cannot derive future encryption keys, thus providing backward secrecy.
Therefore, in the double ratchet algorithm, the KDF ratchet ensures forward secrecy, and the DH ratchet ensures backward secrecy, together achieving both forward and backward secrecy.
We recommend the following video, which provides a more intuitive animation demonstration.
https://youtu.be/9sO2qdTci-s?si=BXLU33BRANWAJKMz
https://youtu.be/7uEeE3TUqmU?si=jpPOR_O61IppgJxl
(We hope users can understand the basic principles to judge for themselves which chat applications are good.)

quoting note1ffg…ntlrMany Nostr users know that the Signal protocol is a very secure end-to-end encryption protocol, recommended by Snowden. However, many people do not know why the Signal protocol is secure. In fact, the design of the Signal protocol has a historical basis and is very intuitive and simple.
End-to-end encryption protocols have gone through three key stages: the PGP (Pretty Good Privacy) protocol of the 1990s, the OTR (Off The Record) protocol of the 2000s, and the Signal protocol of the 201x.
PGP achieved end-to-end encryption through public key encryption. But if a private key leaks, all [past and future] messages can be decrypted. No [forward secrecy] and [backward secrecy].
[[In the PGP protocol, the identity key and the encryption key are the same; it serves as both the identity and is used to encrypt messages.]] [[As an identity key, it is a long-term key, and the longer it is used, the greater the likelihood of private key exposure.]]
The OTR protocol solves the problem of PGP. Its approach is simple: [[it separate the identity key from the encryption key and generates a unique encryption key for each conversation, which is deleted after use.]]
The Signal protocol inherited ideas from the OTR protocol. It mainly consists of two parts: the X3DH protocol, which is responsible for the initial key agreement, and the Double Ratchet Algorithm, which is responsible for deriving encryption keys. [[The Signal protocol derives a new encryption key for each message, which is deleted after use.]] It achieved better forward and backward secrecy.
BTW, the Signal protocol is not equivalent to the Signal app. WhatsApp also uses the Signal protocol for end-to-end encryption. The Signal protocol is only responsible for the end-to-end encryption of messages, meaning only the communicating parties can decrypt the content, not even the server administrators.
