Freedom.Tech on Nostr: Learn how the recent indictment of Tornado Cash founders is not only an immense ...
Learn how the recent indictment of Tornado Cash founders is not only an immense government overreach, but one that shows that governments are getting desperate to stop privacy tools.
Read the full post below to dispel the fog of war 👇
# Tornado Cash indictment shows desperation

Almost precisely one year after the U.S. Treasury [sanctioned the Tornado Cash project and tool itself](https://home.treasury.gov/news/press-releases/jy0916), the U.S. Department of Justice (DOJ) took another monumental leap in the war on privacy by [charging the founders of Tornado Cash](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations) with money transmission, money laundering, and breaking U.S. sanctions law. The rapidly expanding legal aggression against privacy tools for cryptocurrencies like Bitcoin and Ethereum is beginning to show clear signs of desperation by the U.S government. If they can’t outright prevent the use of these decentralized and autonomous tools, they’ll instead turn to legal and regulatory pressure to leverage fear and uncertainty as chilling agents against the privacy-focused developer community.
The DOJ has shown themselves in the indictment to either be willingly manipulating the public by putting forward a false view of Tornado Cash, or simply not understand Tornado Cash at a fundamental technical level. In order to dispel the fog of war being placed by the DOJ in this indictment, let’s walk through what Tornado Cash is and how it works first.
## How does Tornado Cash work?
Tornado Cash is an open-source project that primarily developed and deployed a decentralized smart contract on the Ethereum cryptocurrency blockchain. This smart contract leverages privacy techniques that have been proven out in the Zcash cryptocurrency as extremely effective at protecting the sender, receiver, and amount involved in a transaction, something that Ethereum is notoriously poor at protecting by default. While this smart contract initially allowed the developers to modify and upgrade it in some ways, in [May of 2020 the developers made the smart contract immutable](https://tornado-cash.medium.com/tornado-cash-is-finally-trustless-a6e119c1d1c2). **This immutability is key to understanding what the Tornado Cash founders were (and were not) capable of.**
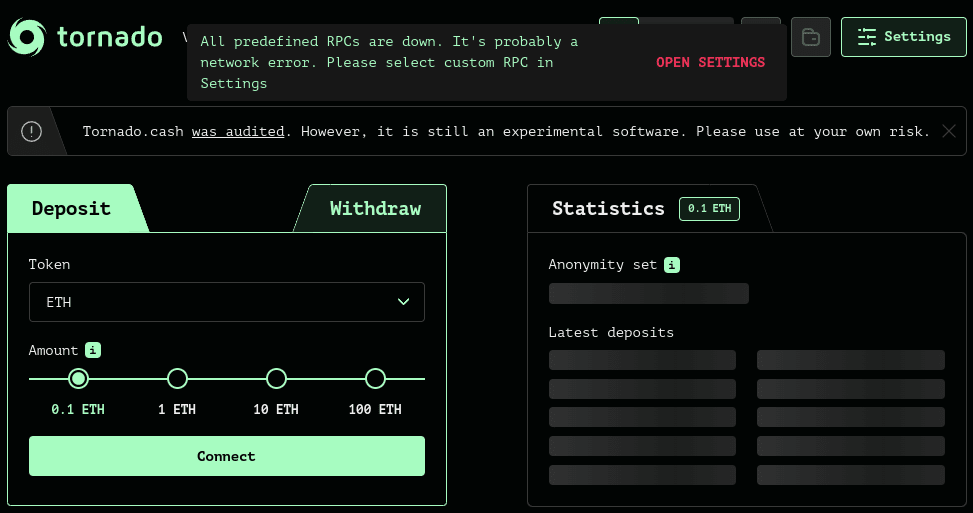
So what did using Tornado Cash actually look like? The vast majority of usage for Tornado Cash came through the web UI that the Tornado Cash founders ran. This web UI enabled non-technical users to easily access the tool and gain privacy on Ethereum, even without running any Ethereum nodes or infrastructure themselves. The process works like this:
1. Select the Tornado Cash “pool” that you wants to use.
1. Pools of 0.1, 1, 10, and 100 ETH were all available.
2. Connect your Ethereum wallet to the Tornado Cash app website via Metamask or similar.
3. The Tornado Cash app generates a random, secret number *locally* that becomes your “secret note.”
1. No other party, including Tornado Cash themselves, ever receive or gain visibility into this secret note. The random number generation and storage all happens on your computer.
2. This secret note can be viewed similarly to a Bitcoin or Ethereum private key, as it alone controls the funds after deposit.
4. You deposit funds and use the secret note **locally** to create a proof that ties the deposited funds to your secret note.
5. When you want to withdraw, you use the secret note **locally** to create a proof of ownership over the funds you deposited ***without revealing which specific funds are yours*** and withdraw them to a fresh Ethereum address.
1. Optionally, you can use a “relayer” in the withdrawal step to avoid having to fund the receiving Ethereum account before withdrawing, for a fee. This relayer never gets visibility of the secret note or custody over funds, and simply acts as a middle-man who pays the necessary Ethereum for you to withdraw your funds and pass the proof generated using the secret note on to the smart contract.
It’s extremely important to realize that this process:
- **Never gives custody of your funds to the Tornado Cash developers, smart contract, or any other third party.**
- **Never reveals the secret note to the Tornado Cash developers, smart contract, or any other third party.**
- **Does not allow you to withdraw anyone else’s funds, but only the exact Ethereum you deposited.**
## Dismantling the charges
With this understanding of the technical function of the Tornado Cash tool and its pieces, we can quickly dismantle the charges against the Tornado Cash founders and see the indictment for what it is — baseless fear-mongering. Here are the charges themselves, directly from the [indictment press release](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations):
> ROMAN STORM, 34, of Auburn, Washington, and ROMAN SEMENOV, 35, a Russian national, are each charged with one count of conspiracy to commit money laundering and one count of conspiracy to violate the International Economic Emergency Powers Act, which each carry a maximum sentence of 20 years in prison. They are also each charged with conspiracy to operate an unlicensed money transmitting business, which carries a maximum sentence of five years in prison.
### Conspiracy to operate an unlicensed money-transmitting business
The entirety of the DOJ’s argument hinges on the last charge, though it carries the lightest sentence. In a fantastic working paper released shortly after the indictment was unsealed, the *[International Academy of Financial Crime Litigators* broke down](https://www.cravath.com/news/the-international-academy-of-financial-crime-litigators-publishes-working-paper-by-cravath-lawyers-on-tornado-cash-indictment.html) what I think is the clearest view of FinCen’s money transmission definition (emphasis theirs):
> This brings to the forefront a crucial distinction: to act as a money transmitter, a party must have necessary ***and*** sufficient control over the value being transmitted.
What is “necessary and sufficient control” you may ask? “Necessary control” in this case can be viewed as the tool being a required component of someone transmitting money. “Sufficient” control can be viewed as the owners of the tool having actual custody and ability to move deposited funds without user interaction. While Tornado Cash absolutely could be considered to have *necessary control* through most users needing to leverage the Tornado Cash web UI that was run by the founders, the function of Tornado Cash explicitly prevented the founders from ever having *sufficient control*.
**Unless the guidance provided by FinCen in 2019 is no longer valid, it seems there is no way that the DOJ could argue truthfully that the Tornado Cash founders ever had both necessary and sufficient control.** Once the charge of money transmission falls apart, the DOJ’s argument that the Tornado Cash founders were responsible for implementing anti-money laundering measures and preventing sanctioned entities from using Tornado Cash quickly disintegrates.
### Conspiracy to commit money laundering
In a previous high-profile case against a cryptocurrency privacy tool — [the “Helix” custodial Bitcoin mixer](https://darkdot.com/articles/helix-bitcoin-mixer/) — the DOJ argued that the core illicit activity was taking custody of customer funds and transmitting them for the user with the aim of providing privacy. This activity is incredibly easy for the government to argue counting as money transmission, and when there is direct profit for the operator involved the trivial next step is to add on a money laundering charge. From the excellent [DarkDot.com](http://darkdot.com/) article on Helix:
> The fact that Helix took complete custody of user’s funds after deposit and then sent them entirely disassociated funds after a delay of about two hours made it an easy target under money transmission laws.
Tornado Cash, however, is an entirely different case. **Neither** **the Tornado Cash founders nor any other third party ever took custody of customer funds, nor do they have any technical means to have done so at any point.** As we walked through earlier, the “secret note” that is used to withdraw funds from Tornado Cash is generated and stored locally by the user and is at no point shared in any way.
To make the absurdity of this claim more vivid, let’s apply it to the use of cash to launder money. If any tool that is used in the act of money laundering is considered complicit, why don’t we also indict the makers of armored trucks that are used to move cash for banks? While armored cars may be *necessary* for banks to launder money, they never have *sufficient control* as the manufacturer doesn't take custody of funds – only the bank does.
Banks are by [far the largest conspirators in the act of money laundering globally](https://www.theguardian.com/world/2011/apr/03/us-bank-mexico-drug-gangs), and yet we don’t fault any of the service providers or manufacturers whose products are used in these money laundering schemes. Unlike most [banking-related money laundering cases](https://www.reuters.com/legal/danske-bank-pleads-guilty-resolve-long-running-estonia-money-laundering-probe-2022-12-13/), however, **the DOJ seeks to hold an individual accountable for merely building a tool that was allegedly used for money laundering by North Korean hackers.**
### Conspiracy to violate the International Economic Emergency Powers Act
And lastly, we have the charge related to the U.S. Treasury sanctions placed on Tornado Cash as a whole in August of 2022. This charge is that the founders of Tornado Cash “knowingly and willfully” aided and allowed North Korean hackers to move funds through Tornado Cash. While we’ve already clearly laid out how they never had custody of funds (something more important for money transmission charges), the most important question to answer for this charge is “did the Tornado Cash founders have any technical means available to prevent usage of Tornado Cash by sanctioned entities?”
A key aspect of the Tornado Cash operation that we haven’t touched on is that there are two ways to interact with Tornado Cash as a tool — you can either leverage the web UI that the founders hosted, or you can interact directly with the immutable, decentralized smart contract on Ethereum. While the Tornado Cash founders could (and did) attempt to block usage of the Tornado Cash web UI, **they had no control over the smart contract and thus no ability to prevent its direct usage.**
The Tornado Cash founders did take the active step of [implementing a Chainalysis-built sanctions tool](https://twitter.com/TornadoCash/status/1514904975037669386) into the web UI within 24 hours of the sanctioning of the North Korean hacking group “Lazarus.” While this step made it more difficult for sanctioned entities to utilize Tornado Cash, it cannot technically prevent sanctioned entities from using the smart contract directly. Only Ethereum validators could do that, something that would require a complete change in Ethereum’s consensus. The DOJ glaringly makes no mention of whether the North Korean hackers used the web UI or the smart contract directly for their usage of Tornado Cash, something that is vital to determining the role the founders could have played.
But ask yourself this question: **do you really think that a hacking group credited with at least [$1.7b in complex and technical hacks in 2022 alone](https://www.chainalysis.com/blog/2022-biggest-year-ever-for-crypto-hacking/) would be incapable of using the Ethereum smart contract directly?** The Lazarus group has proven a deep knowledge of the Ethereum ecosystem and network, and absolutely has the resources and technical know-how to circumvent the censorable web UI of Tornado Cash entirely. If the Tornado Cash founders have no way to prevent their direct usage of the smart contract, and it’s in the Lazarus group’s best interest to use the smart contract directly, how can the Tornado Cash founders be held liable?
## A reek of desperation
When we pull back the veil the DOJ seems to want to keep over our eyes in this indictment, it becomes abundantly clear that there is no realistic case to be had here. None of the three counts the Tornado Cash founders are being charged with hold any water, and as such, we have to look at ulterior motives. The U.S. government seems to have clearly recognized that they have no trivial means at their disposal to prevent the usage of decentralized, non-custodial privacy tools, and instead have turned to fear as their primary agent instead of fair justice.
The U.S. government appears to be seeking to stifle innovation and development of decentralized privacy tools, sowing doubt in every developer's mind with one simple question: “if the tool I create is used for illicit activity, will I be held liable?” If developers who publish free speech in the form of code can be held liable for the way that their tool is used ***despite no ability to prevent illicit usage***, it sets a horrifying and oppressive precedent.
The DOJ can claim almost anything they’d like in an indictment, but thankfully, there is still a justice system that will see and rule on this case in the coming months and years. The indictment itself may be discouraging, but we have yet to see how the case itself will actually be ruled. Our hope is that the U.S. justice system will see through the desperation and fallacies put forth in the DOJ’s indictment and will rule in favor of code as free speech.
## What you can do
While it’s always valuable to sit and ponder the philosophical and moral aspects of situations like this, it’s even more pertinent and valuable to take actionable steps to help stem the tide in the war on privacy. Accessible and useful privacy tools are ***essential*** *to human freedom* and must be fought for. So what are some ways that you can pitch in and help protect our right to privacy?
> Privacy only extends so far as the cooperation of one's fellows in society. - *A Cypherpunk's Manifesto*
### Be optimistic
It may not be immediately apparent, but one of the biggest takeaways is quite simple – **we're winning.** The fact that a massive government like the U.S. feels threatened enough by privacy tools to take overt legal action shows that the powerful tools being built out to empower you, the user, are working. The immense uptake of privacy tools like Signal, Proton Mail, and the Tor network have started to shift the balance of power back towards the individual.
**The more push-back and fight we see from governments across the globe against encryption and privacy-preserving tools, the more evidence we have that the tools are actually working.**
### Let your voice be heard
The simplest way that you can contribute to this fight is to loudly and publicly show support for privacy developers and projects. Stepping out of line and making it clear that you won’t silently allow governments to unjustly target privacy tools and their developers forces governments to make a choice — keep citizens happy or continue to overtly strip them of their privacy. While the cynical among us might assume governments will continue waging a war on privacy, bringing their efforts into the light and exposing them to a much broader portion of the world helps to disincentivize governments from further similar actions.
This type of incredible overreach by the government would be most useful to those in power if we stayed silent and simply allowed it to happen in the background. **But we will not remain silent.** We must be willing to cross community, project, and ideological divides to band together and fight back against this tyranny.
### Support privacy developers and projects
At times like these, it can be daunting and discouraging to work on privacy tech. A simple way that we can help prevent the chilling effect the U.S. government seems to want to put in place is to vocally show support for those working tirelessly to build privacy tools. That can look like simple words of encouragement (publicly or privately), [donations to projects you love](https://freedom.tech/supporting-freedom-tech/), or stepping in to take on simple tasks or issues yourself for those same projects.
### Don’t let them chill your free speech
If you’re already a developer in the space or someone considering building out privacy tools, I understand how daunting it can be to read this indictment and still build on. But keep in mind that there is a long-standing precedent of **[code as free speech](https://www.notion.so/Tornado-Cash-indictment-shows-desperation-4522cd9f66cb458f9e879c954c6f93da?pvs=21)**. Developers cannot, and should not, be held liable for how their speech is leveraged by others, and this Tornado Cash case will hopefully only reinforce that precedent if justice prevails. There are no more timely words for this situation than those of Eric Hughes in *A Cypherpunk's Manifesto,* written 30 years ago*:*
> Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it… We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
In times where governments are actively attacking privacy technologies and tools across the globe, we need now more than ever altruistic and motivated developers and communities to spring up and build, improve, and maintain the tools we need to retain and fight for our freedom.
“Let us proceed together apace. Onward.”
This post was originally published in full on freedom.tech: https://freedom.tech/tornado-cash-indictment-shows-desperation/
## Join the conversation
Want to jump in and connect with other like-minded people in the freedom tech community? Join our Signal (npub1n03…h0ky) or simplex (npub1exv…d828) group chats today:
https://freedom.tech/join-the-conversation/
Read the full post below to dispel the fog of war 👇
# Tornado Cash indictment shows desperation

Almost precisely one year after the U.S. Treasury [sanctioned the Tornado Cash project and tool itself](https://home.treasury.gov/news/press-releases/jy0916), the U.S. Department of Justice (DOJ) took another monumental leap in the war on privacy by [charging the founders of Tornado Cash](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations) with money transmission, money laundering, and breaking U.S. sanctions law. The rapidly expanding legal aggression against privacy tools for cryptocurrencies like Bitcoin and Ethereum is beginning to show clear signs of desperation by the U.S government. If they can’t outright prevent the use of these decentralized and autonomous tools, they’ll instead turn to legal and regulatory pressure to leverage fear and uncertainty as chilling agents against the privacy-focused developer community.
The DOJ has shown themselves in the indictment to either be willingly manipulating the public by putting forward a false view of Tornado Cash, or simply not understand Tornado Cash at a fundamental technical level. In order to dispel the fog of war being placed by the DOJ in this indictment, let’s walk through what Tornado Cash is and how it works first.
## How does Tornado Cash work?
Tornado Cash is an open-source project that primarily developed and deployed a decentralized smart contract on the Ethereum cryptocurrency blockchain. This smart contract leverages privacy techniques that have been proven out in the Zcash cryptocurrency as extremely effective at protecting the sender, receiver, and amount involved in a transaction, something that Ethereum is notoriously poor at protecting by default. While this smart contract initially allowed the developers to modify and upgrade it in some ways, in [May of 2020 the developers made the smart contract immutable](https://tornado-cash.medium.com/tornado-cash-is-finally-trustless-a6e119c1d1c2). **This immutability is key to understanding what the Tornado Cash founders were (and were not) capable of.**

So what did using Tornado Cash actually look like? The vast majority of usage for Tornado Cash came through the web UI that the Tornado Cash founders ran. This web UI enabled non-technical users to easily access the tool and gain privacy on Ethereum, even without running any Ethereum nodes or infrastructure themselves. The process works like this:
1. Select the Tornado Cash “pool” that you wants to use.
1. Pools of 0.1, 1, 10, and 100 ETH were all available.
2. Connect your Ethereum wallet to the Tornado Cash app website via Metamask or similar.
3. The Tornado Cash app generates a random, secret number *locally* that becomes your “secret note.”
1. No other party, including Tornado Cash themselves, ever receive or gain visibility into this secret note. The random number generation and storage all happens on your computer.
2. This secret note can be viewed similarly to a Bitcoin or Ethereum private key, as it alone controls the funds after deposit.
4. You deposit funds and use the secret note **locally** to create a proof that ties the deposited funds to your secret note.
5. When you want to withdraw, you use the secret note **locally** to create a proof of ownership over the funds you deposited ***without revealing which specific funds are yours*** and withdraw them to a fresh Ethereum address.
1. Optionally, you can use a “relayer” in the withdrawal step to avoid having to fund the receiving Ethereum account before withdrawing, for a fee. This relayer never gets visibility of the secret note or custody over funds, and simply acts as a middle-man who pays the necessary Ethereum for you to withdraw your funds and pass the proof generated using the secret note on to the smart contract.
It’s extremely important to realize that this process:
- **Never gives custody of your funds to the Tornado Cash developers, smart contract, or any other third party.**
- **Never reveals the secret note to the Tornado Cash developers, smart contract, or any other third party.**
- **Does not allow you to withdraw anyone else’s funds, but only the exact Ethereum you deposited.**
## Dismantling the charges
With this understanding of the technical function of the Tornado Cash tool and its pieces, we can quickly dismantle the charges against the Tornado Cash founders and see the indictment for what it is — baseless fear-mongering. Here are the charges themselves, directly from the [indictment press release](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations):
> ROMAN STORM, 34, of Auburn, Washington, and ROMAN SEMENOV, 35, a Russian national, are each charged with one count of conspiracy to commit money laundering and one count of conspiracy to violate the International Economic Emergency Powers Act, which each carry a maximum sentence of 20 years in prison. They are also each charged with conspiracy to operate an unlicensed money transmitting business, which carries a maximum sentence of five years in prison.
### Conspiracy to operate an unlicensed money-transmitting business
The entirety of the DOJ’s argument hinges on the last charge, though it carries the lightest sentence. In a fantastic working paper released shortly after the indictment was unsealed, the *[International Academy of Financial Crime Litigators* broke down](https://www.cravath.com/news/the-international-academy-of-financial-crime-litigators-publishes-working-paper-by-cravath-lawyers-on-tornado-cash-indictment.html) what I think is the clearest view of FinCen’s money transmission definition (emphasis theirs):
> This brings to the forefront a crucial distinction: to act as a money transmitter, a party must have necessary ***and*** sufficient control over the value being transmitted.
What is “necessary and sufficient control” you may ask? “Necessary control” in this case can be viewed as the tool being a required component of someone transmitting money. “Sufficient” control can be viewed as the owners of the tool having actual custody and ability to move deposited funds without user interaction. While Tornado Cash absolutely could be considered to have *necessary control* through most users needing to leverage the Tornado Cash web UI that was run by the founders, the function of Tornado Cash explicitly prevented the founders from ever having *sufficient control*.
**Unless the guidance provided by FinCen in 2019 is no longer valid, it seems there is no way that the DOJ could argue truthfully that the Tornado Cash founders ever had both necessary and sufficient control.** Once the charge of money transmission falls apart, the DOJ’s argument that the Tornado Cash founders were responsible for implementing anti-money laundering measures and preventing sanctioned entities from using Tornado Cash quickly disintegrates.
### Conspiracy to commit money laundering
In a previous high-profile case against a cryptocurrency privacy tool — [the “Helix” custodial Bitcoin mixer](https://darkdot.com/articles/helix-bitcoin-mixer/) — the DOJ argued that the core illicit activity was taking custody of customer funds and transmitting them for the user with the aim of providing privacy. This activity is incredibly easy for the government to argue counting as money transmission, and when there is direct profit for the operator involved the trivial next step is to add on a money laundering charge. From the excellent [DarkDot.com](http://darkdot.com/) article on Helix:
> The fact that Helix took complete custody of user’s funds after deposit and then sent them entirely disassociated funds after a delay of about two hours made it an easy target under money transmission laws.
Tornado Cash, however, is an entirely different case. **Neither** **the Tornado Cash founders nor any other third party ever took custody of customer funds, nor do they have any technical means to have done so at any point.** As we walked through earlier, the “secret note” that is used to withdraw funds from Tornado Cash is generated and stored locally by the user and is at no point shared in any way.
To make the absurdity of this claim more vivid, let’s apply it to the use of cash to launder money. If any tool that is used in the act of money laundering is considered complicit, why don’t we also indict the makers of armored trucks that are used to move cash for banks? While armored cars may be *necessary* for banks to launder money, they never have *sufficient control* as the manufacturer doesn't take custody of funds – only the bank does.
Banks are by [far the largest conspirators in the act of money laundering globally](https://www.theguardian.com/world/2011/apr/03/us-bank-mexico-drug-gangs), and yet we don’t fault any of the service providers or manufacturers whose products are used in these money laundering schemes. Unlike most [banking-related money laundering cases](https://www.reuters.com/legal/danske-bank-pleads-guilty-resolve-long-running-estonia-money-laundering-probe-2022-12-13/), however, **the DOJ seeks to hold an individual accountable for merely building a tool that was allegedly used for money laundering by North Korean hackers.**
### Conspiracy to violate the International Economic Emergency Powers Act
And lastly, we have the charge related to the U.S. Treasury sanctions placed on Tornado Cash as a whole in August of 2022. This charge is that the founders of Tornado Cash “knowingly and willfully” aided and allowed North Korean hackers to move funds through Tornado Cash. While we’ve already clearly laid out how they never had custody of funds (something more important for money transmission charges), the most important question to answer for this charge is “did the Tornado Cash founders have any technical means available to prevent usage of Tornado Cash by sanctioned entities?”
A key aspect of the Tornado Cash operation that we haven’t touched on is that there are two ways to interact with Tornado Cash as a tool — you can either leverage the web UI that the founders hosted, or you can interact directly with the immutable, decentralized smart contract on Ethereum. While the Tornado Cash founders could (and did) attempt to block usage of the Tornado Cash web UI, **they had no control over the smart contract and thus no ability to prevent its direct usage.**
The Tornado Cash founders did take the active step of [implementing a Chainalysis-built sanctions tool](https://twitter.com/TornadoCash/status/1514904975037669386) into the web UI within 24 hours of the sanctioning of the North Korean hacking group “Lazarus.” While this step made it more difficult for sanctioned entities to utilize Tornado Cash, it cannot technically prevent sanctioned entities from using the smart contract directly. Only Ethereum validators could do that, something that would require a complete change in Ethereum’s consensus. The DOJ glaringly makes no mention of whether the North Korean hackers used the web UI or the smart contract directly for their usage of Tornado Cash, something that is vital to determining the role the founders could have played.
But ask yourself this question: **do you really think that a hacking group credited with at least [$1.7b in complex and technical hacks in 2022 alone](https://www.chainalysis.com/blog/2022-biggest-year-ever-for-crypto-hacking/) would be incapable of using the Ethereum smart contract directly?** The Lazarus group has proven a deep knowledge of the Ethereum ecosystem and network, and absolutely has the resources and technical know-how to circumvent the censorable web UI of Tornado Cash entirely. If the Tornado Cash founders have no way to prevent their direct usage of the smart contract, and it’s in the Lazarus group’s best interest to use the smart contract directly, how can the Tornado Cash founders be held liable?
## A reek of desperation
When we pull back the veil the DOJ seems to want to keep over our eyes in this indictment, it becomes abundantly clear that there is no realistic case to be had here. None of the three counts the Tornado Cash founders are being charged with hold any water, and as such, we have to look at ulterior motives. The U.S. government seems to have clearly recognized that they have no trivial means at their disposal to prevent the usage of decentralized, non-custodial privacy tools, and instead have turned to fear as their primary agent instead of fair justice.
The U.S. government appears to be seeking to stifle innovation and development of decentralized privacy tools, sowing doubt in every developer's mind with one simple question: “if the tool I create is used for illicit activity, will I be held liable?” If developers who publish free speech in the form of code can be held liable for the way that their tool is used ***despite no ability to prevent illicit usage***, it sets a horrifying and oppressive precedent.
The DOJ can claim almost anything they’d like in an indictment, but thankfully, there is still a justice system that will see and rule on this case in the coming months and years. The indictment itself may be discouraging, but we have yet to see how the case itself will actually be ruled. Our hope is that the U.S. justice system will see through the desperation and fallacies put forth in the DOJ’s indictment and will rule in favor of code as free speech.
## What you can do
While it’s always valuable to sit and ponder the philosophical and moral aspects of situations like this, it’s even more pertinent and valuable to take actionable steps to help stem the tide in the war on privacy. Accessible and useful privacy tools are ***essential*** *to human freedom* and must be fought for. So what are some ways that you can pitch in and help protect our right to privacy?
> Privacy only extends so far as the cooperation of one's fellows in society. - *A Cypherpunk's Manifesto*
### Be optimistic
It may not be immediately apparent, but one of the biggest takeaways is quite simple – **we're winning.** The fact that a massive government like the U.S. feels threatened enough by privacy tools to take overt legal action shows that the powerful tools being built out to empower you, the user, are working. The immense uptake of privacy tools like Signal, Proton Mail, and the Tor network have started to shift the balance of power back towards the individual.
**The more push-back and fight we see from governments across the globe against encryption and privacy-preserving tools, the more evidence we have that the tools are actually working.**
### Let your voice be heard
The simplest way that you can contribute to this fight is to loudly and publicly show support for privacy developers and projects. Stepping out of line and making it clear that you won’t silently allow governments to unjustly target privacy tools and their developers forces governments to make a choice — keep citizens happy or continue to overtly strip them of their privacy. While the cynical among us might assume governments will continue waging a war on privacy, bringing their efforts into the light and exposing them to a much broader portion of the world helps to disincentivize governments from further similar actions.
This type of incredible overreach by the government would be most useful to those in power if we stayed silent and simply allowed it to happen in the background. **But we will not remain silent.** We must be willing to cross community, project, and ideological divides to band together and fight back against this tyranny.
### Support privacy developers and projects
At times like these, it can be daunting and discouraging to work on privacy tech. A simple way that we can help prevent the chilling effect the U.S. government seems to want to put in place is to vocally show support for those working tirelessly to build privacy tools. That can look like simple words of encouragement (publicly or privately), [donations to projects you love](https://freedom.tech/supporting-freedom-tech/), or stepping in to take on simple tasks or issues yourself for those same projects.
### Don’t let them chill your free speech
If you’re already a developer in the space or someone considering building out privacy tools, I understand how daunting it can be to read this indictment and still build on. But keep in mind that there is a long-standing precedent of **[code as free speech](https://www.notion.so/Tornado-Cash-indictment-shows-desperation-4522cd9f66cb458f9e879c954c6f93da?pvs=21)**. Developers cannot, and should not, be held liable for how their speech is leveraged by others, and this Tornado Cash case will hopefully only reinforce that precedent if justice prevails. There are no more timely words for this situation than those of Eric Hughes in *A Cypherpunk's Manifesto,* written 30 years ago*:*
> Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it… We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
In times where governments are actively attacking privacy technologies and tools across the globe, we need now more than ever altruistic and motivated developers and communities to spring up and build, improve, and maintain the tools we need to retain and fight for our freedom.
“Let us proceed together apace. Onward.”
This post was originally published in full on freedom.tech: https://freedom.tech/tornado-cash-indictment-shows-desperation/
## Join the conversation
Want to jump in and connect with other like-minded people in the freedom tech community? Join our Signal (npub1n03…h0ky) or simplex (npub1exv…d828) group chats today:
https://freedom.tech/join-the-conversation/
