arcanicanis on Nostr: So here’s an example of one of the maliciously-crafted payloads that resulted in a ...
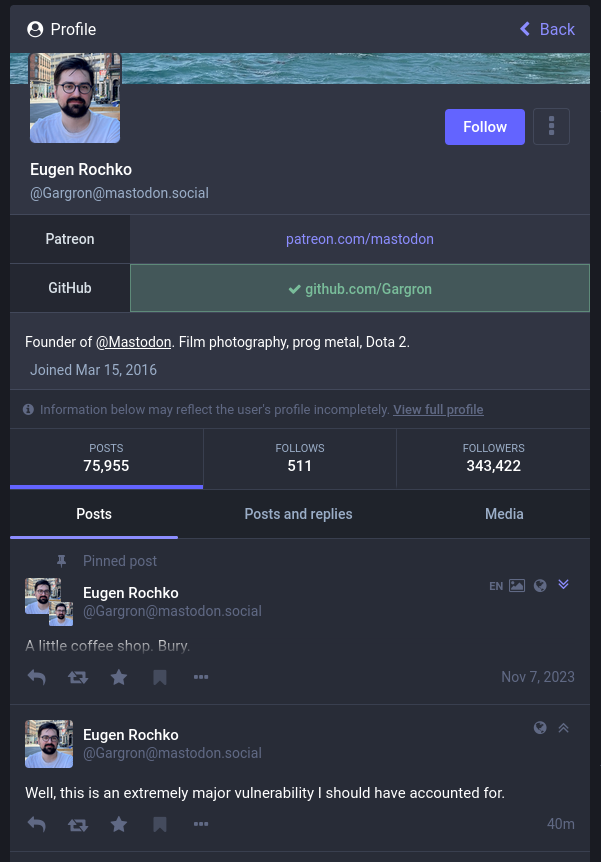
So here’s an example of one of the maliciously-crafted payloads that resulted in a 9.8 severity CVE (CVE-2024-23832) against Mastodon:
{
"@context": ["https://www.w3.org/ns/activitystreams";],
"id": "https://mastodon.social/users/Gargron/posts/123456";,
"type": "Note",
"actor": "https://mastodon.social/users/Gargron";,
"attributedTo": "https://mastodon.social/users/Gargron";,
"content": "Well, this is an extremely concerning vulnerability I should have accounted for.",
"to": [ "https://www.w3.org/ns/activitystreams#Public"; ],
"cc": [ "https://mastodon.social/users/Gargron/followers"; ],
"published": "2024-01-28T22:00:00Z"
}
I have previously double-checked with one of the Mastodon developers (while CC’ing the Mastodon Security email) to confirm that I’m free to release the details at this scheduled time (Feb 15th 15:00 UTC). According to the current observed metrics on FediDB, >73.6% of Mastodon instances are patched against CVE-2024-23832, as manually tabulated.
For more details on the vulnerability, the original security report as it was submitted on Github is available at: https://arcanican.is/excerpts/cve-2024-23832/
My recount of events (as well as unsolicited commentary and criticisms on the vulnerability, ecosystem, etc; when I get around to finishing it): https://arcanican.is/excerpts/cve-2024-23832/discovery.htm
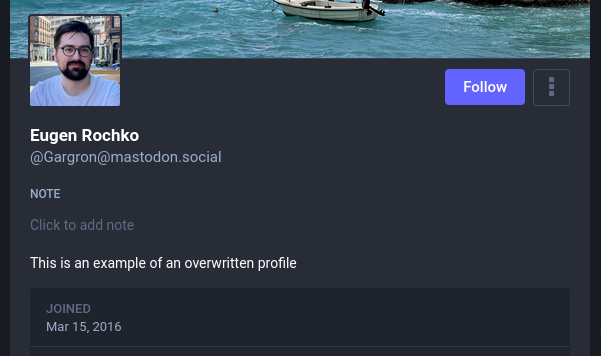
{
"@context": ["https://www.w3.org/ns/activitystreams";],
"id": "https://mastodon.social/users/Gargron/posts/123456";,
"type": "Note",
"actor": "https://mastodon.social/users/Gargron";,
"attributedTo": "https://mastodon.social/users/Gargron";,
"content": "Well, this is an extremely concerning vulnerability I should have accounted for.",
"to": [ "https://www.w3.org/ns/activitystreams#Public"; ],
"cc": [ "https://mastodon.social/users/Gargron/followers"; ],
"published": "2024-01-28T22:00:00Z"
}
I have previously double-checked with one of the Mastodon developers (while CC’ing the Mastodon Security email) to confirm that I’m free to release the details at this scheduled time (Feb 15th 15:00 UTC). According to the current observed metrics on FediDB, >73.6% of Mastodon instances are patched against CVE-2024-23832, as manually tabulated.
For more details on the vulnerability, the original security report as it was submitted on Github is available at: https://arcanican.is/excerpts/cve-2024-23832/
My recount of events (as well as unsolicited commentary and criticisms on the vulnerability, ecosystem, etc; when I get around to finishing it): https://arcanican.is/excerpts/cve-2024-23832/discovery.htm


