Alex on Nostr: I have taken a very unusual and extreme approach, but I think it's a good one: do not ...
I have taken a very unusual and extreme approach, but I think it's a good one: do not allow users to export their private key. If they generate a key through my client, I show it to them exactly once, and then don't allow them to access it again.
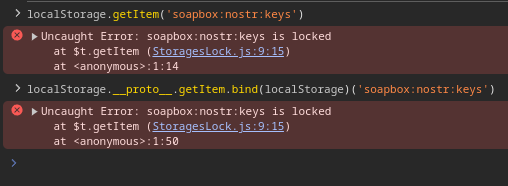
I have even taken it a step further, and prevent _scripts_ from being able to access the key in localStorage after the page has loaded.
(See: https://gitlab.com/soapbox-pub/weblock/-/blob/main/src/StoragesLock.ts )
However, I don't have any red text that says "Do not use this, it's insecure". My wife says this is a "Dead dove do not eat" moment: https://www.youtube.com/watch?v=YUKmq7UMJys
In my case I am actually expecting users to paste private keys as an acceptable part of the flow. So I had to take all these precautions.
If you want to let people export their key, then keep the red warning text, don't lock the storage, and then only access the storage directly when people are on that specific part of the UI where they need to export their key.
I have even taken it a step further, and prevent _scripts_ from being able to access the key in localStorage after the page has loaded.
quoting nevent1q…6nx5There is probably some way for an attacker to get around this. But I made a best effort to modify the global JavaScript API in the browser to prevent access to specific items in localStorage.
Basically as soon as possible into the page loading, we get the value and make it a private property of a NostrSigner object (so you can only call methods like getPublicKey, signEvent, etc), then we lock the key from being accessed again. An XSS attack would have to load prior to this script getting called, or do some JS trickery I haven't considered.
(See: https://gitlab.com/soapbox-pub/weblock/-/blob/main/src/StoragesLock.ts )
However, I don't have any red text that says "Do not use this, it's insecure". My wife says this is a "Dead dove do not eat" moment: https://www.youtube.com/watch?v=YUKmq7UMJys
In my case I am actually expecting users to paste private keys as an acceptable part of the flow. So I had to take all these precautions.
If you want to let people export their key, then keep the red warning text, don't lock the storage, and then only access the storage directly when people are on that specific part of the UI where they need to export their key.
