SimplifiedPrivacy.com on Nostr: Crypto-Anarchy 101: (as Pictures) Get one easy to understand Picture for each ...
Crypto-Anarchy 101: (as Pictures)
Get one easy to understand Picture for each protocol:

Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.
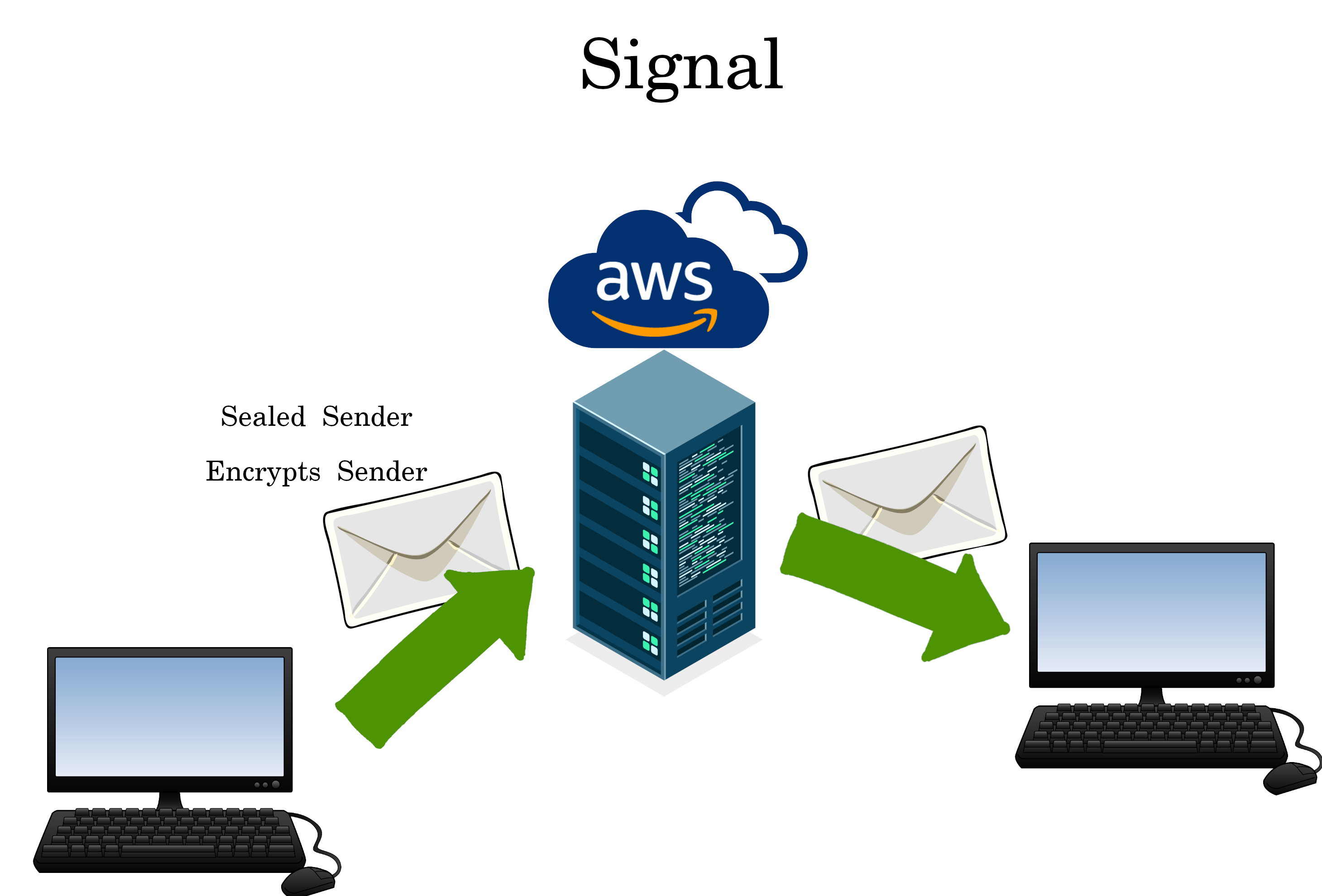
Learn Tips for Signal: https://simplifiedprivacy.com/signal/index.html
~~
XMPP
XMPP is well-trusted, but the OMEMO encryption dies with the domain it’s linked to. This means XMPP is nothing more than end-to-end encrypted email (with rotating keys).
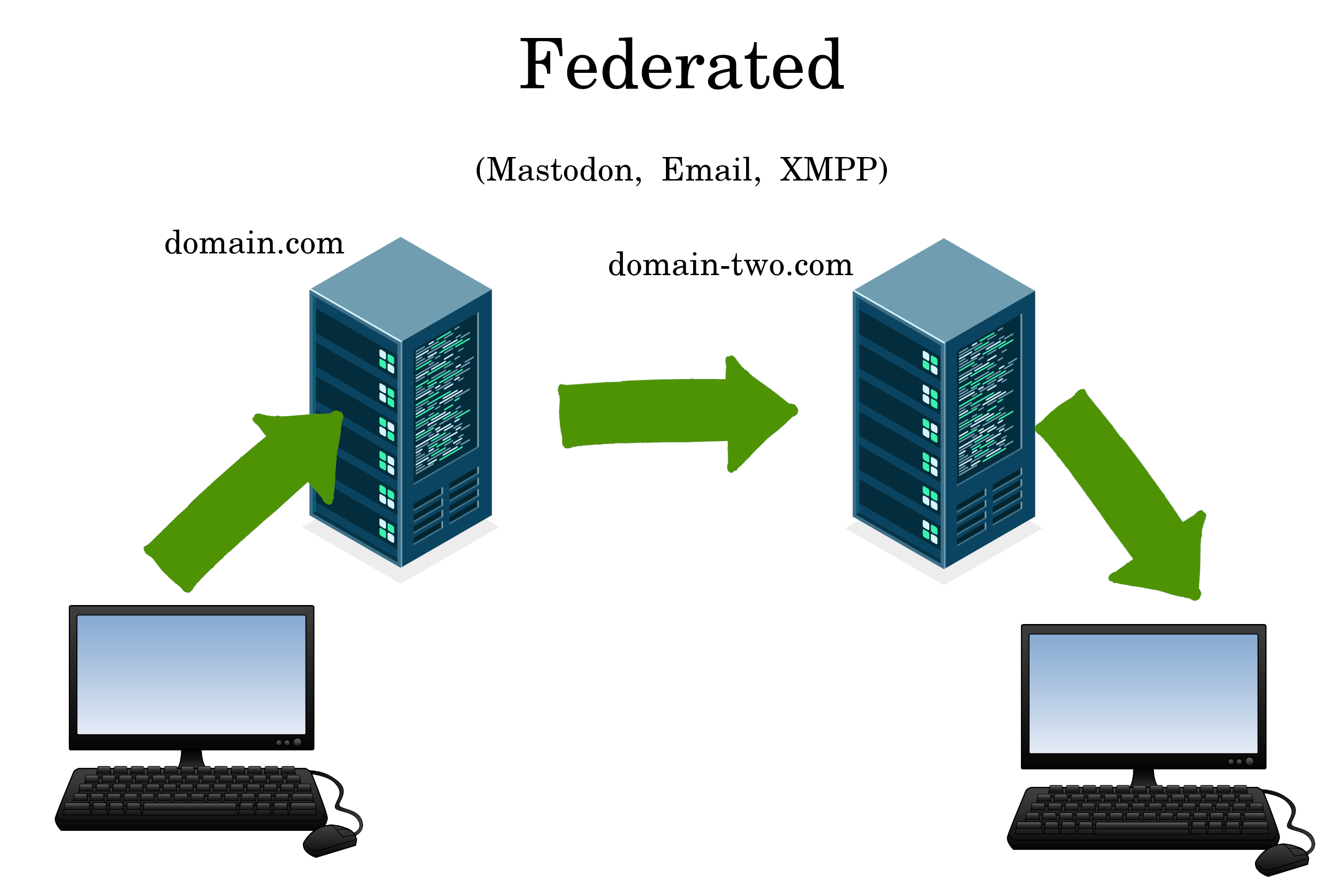
Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.
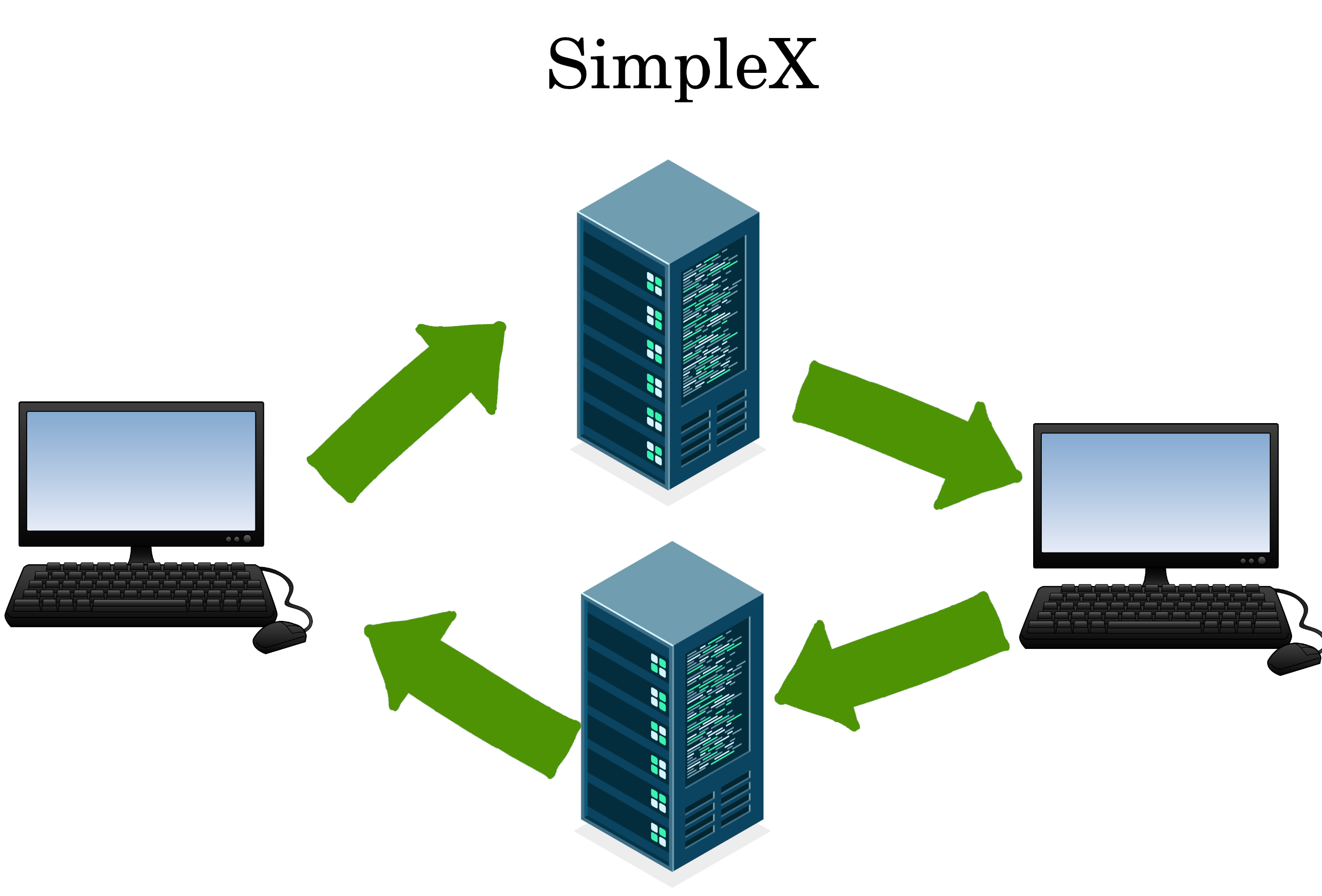
SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.
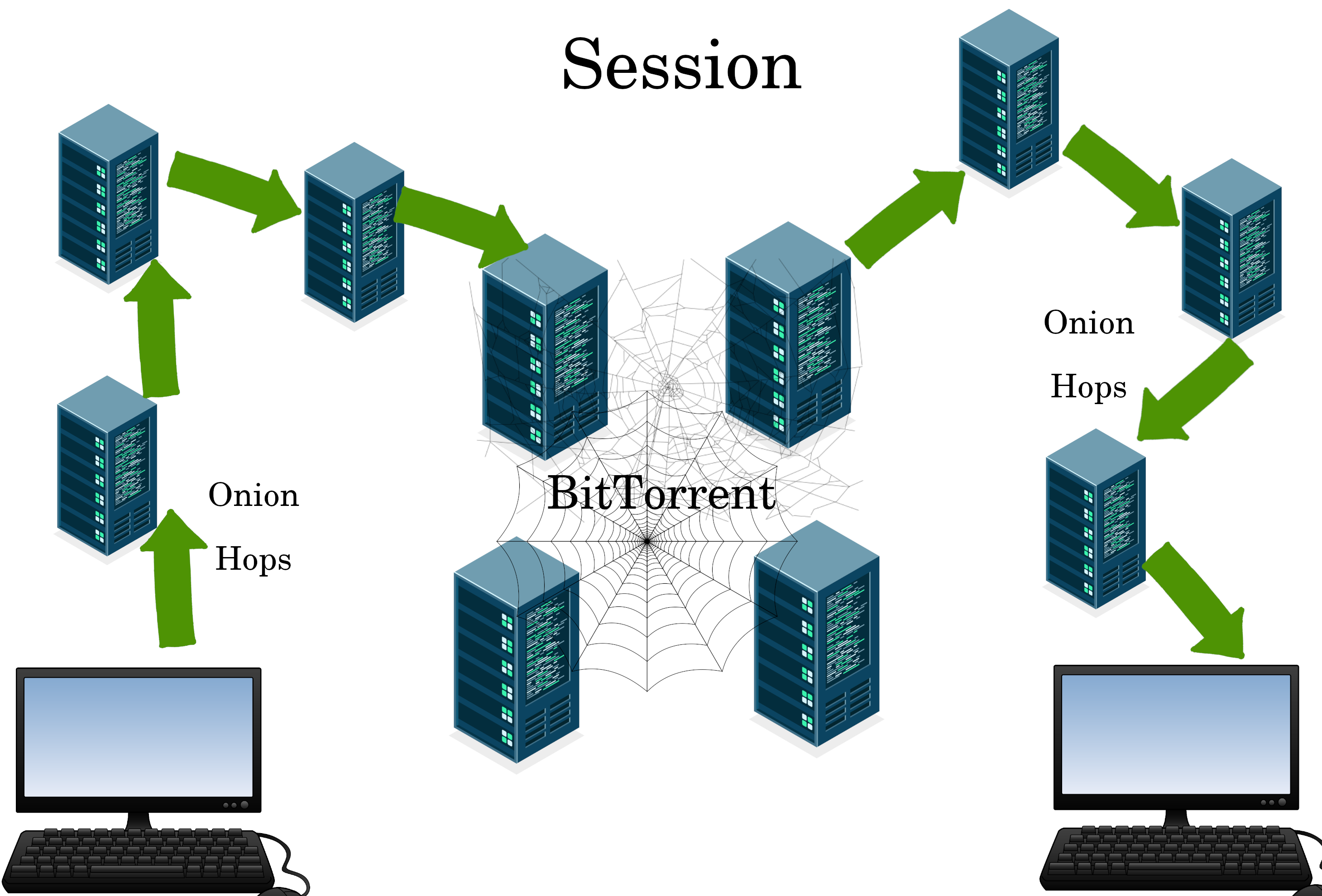
We use Session for an uncensored email list: https://simplifiedprivacy.com/uncensored/index.html
~~
Arweave
Arweave is to websites, what Session is to messages. Both have nodes being paid in a crypto to host a BitTorrent database. The main difference is Arweave stores the data DIRECTLY ON the blockchain.. and potentially forever.
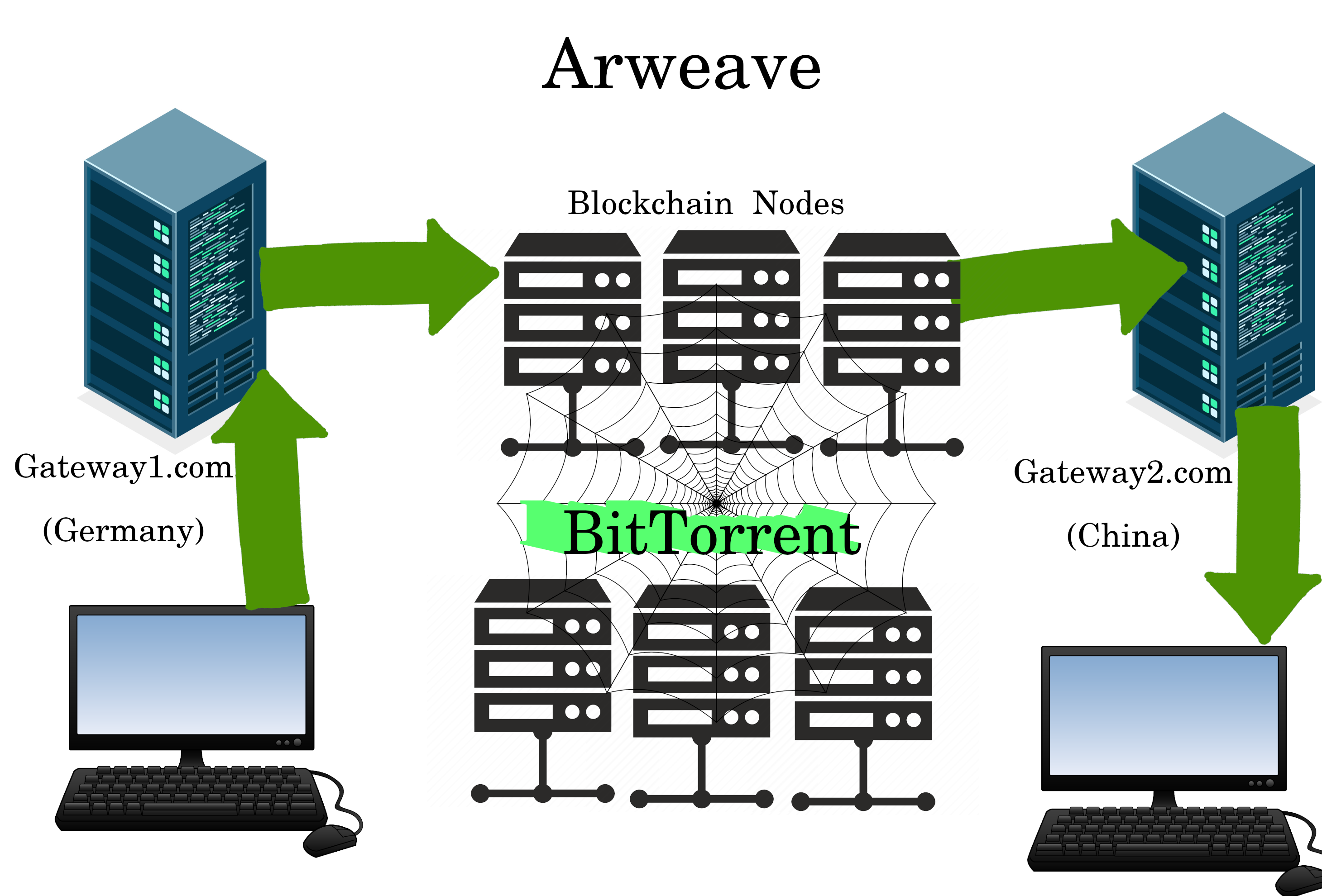
Learn about Arweave here: https://simplifiedprivacy.com/arweave/Arweave-QA/index.html
~~
Nostr
Nostr has no blockchain. Users cryptographically sign messages, and then directly post and receive from relays.
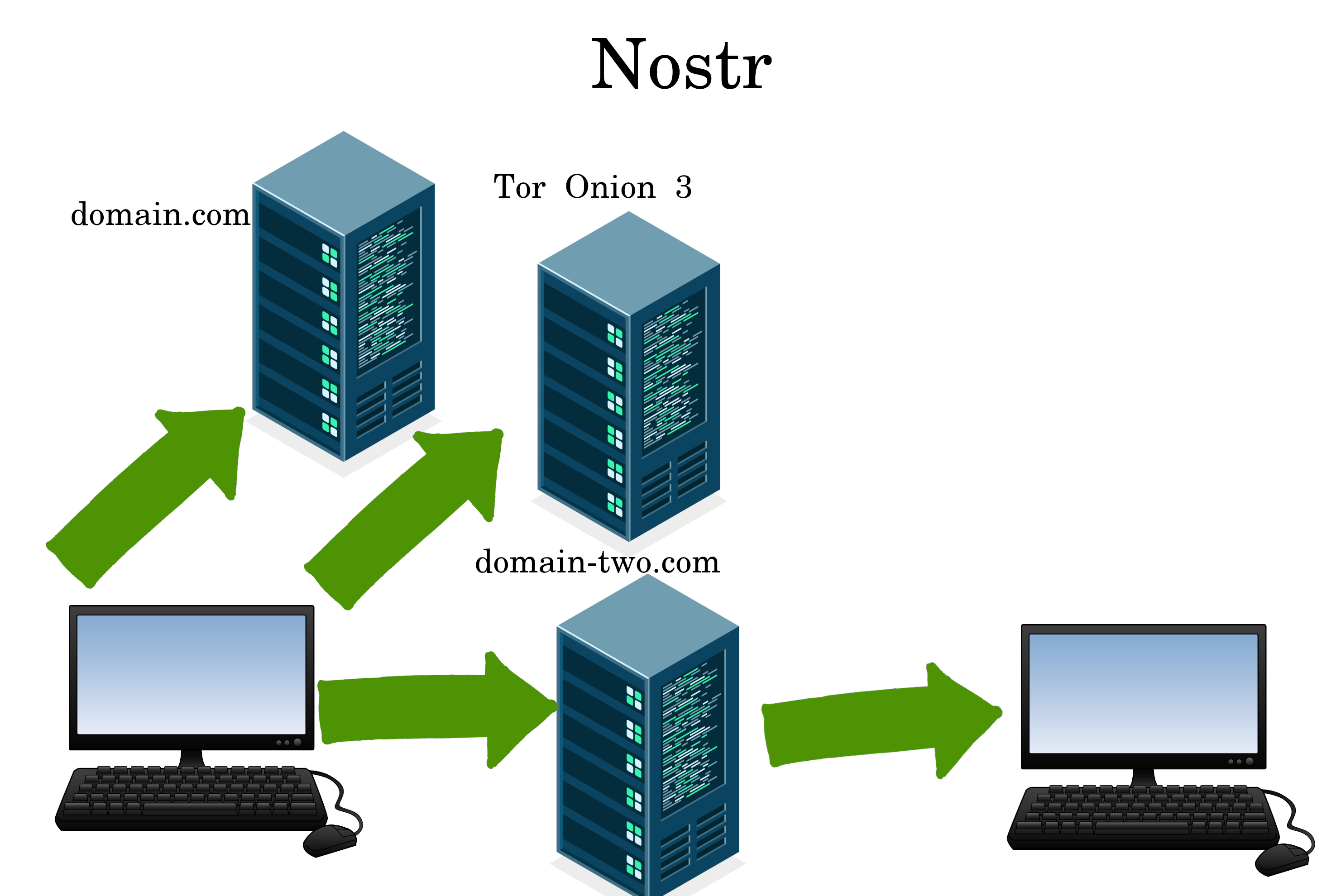
Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).
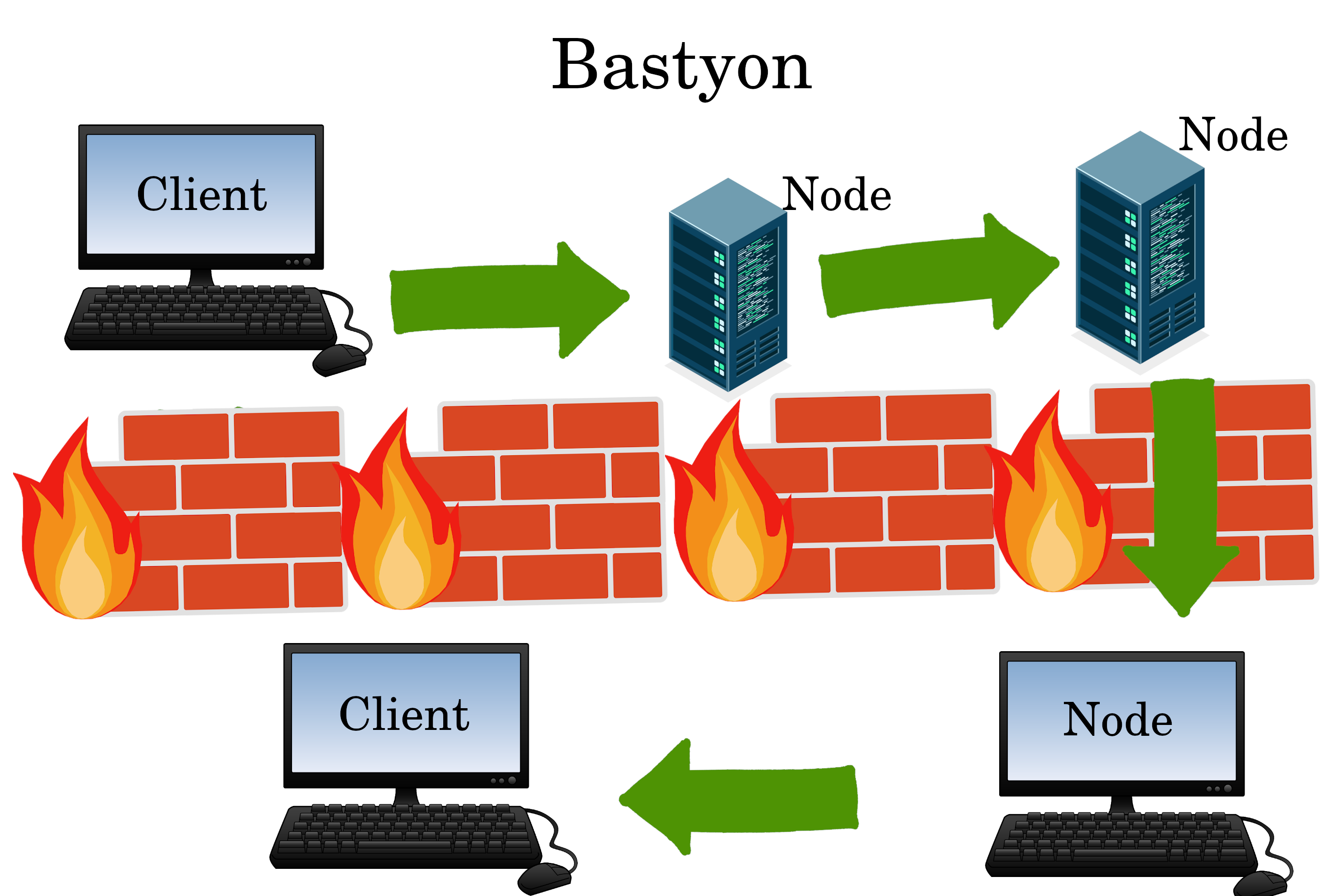
Learn about Bastyon here: https://simplifiedprivacy.com/bastyon-works/how.html
~~
Bitcoin Lightning
Lightning Channels are like an Abacus, keeping track of who owes who on the Layer 1. It does multiple hops for privacy, similar to Tor.
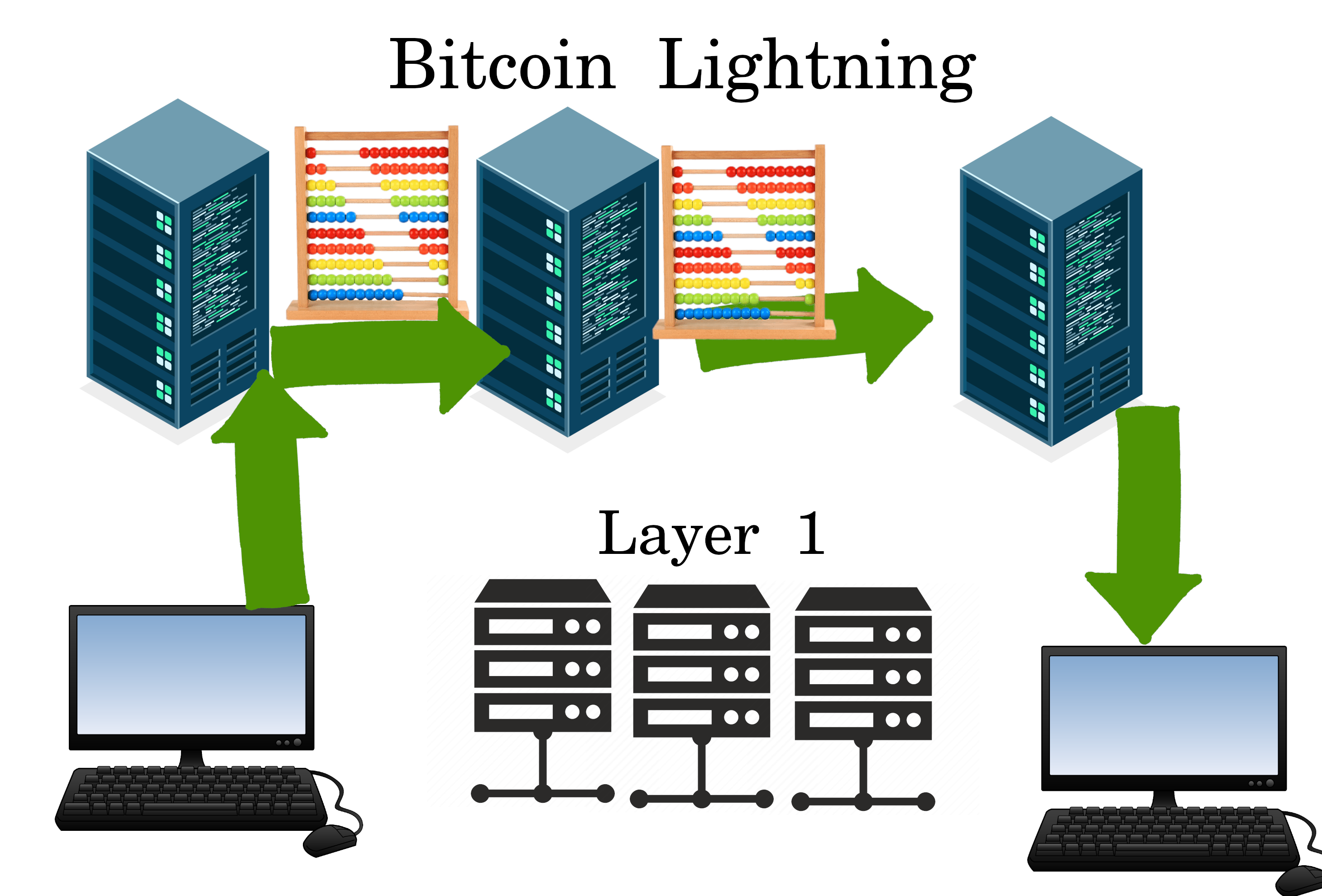
~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.
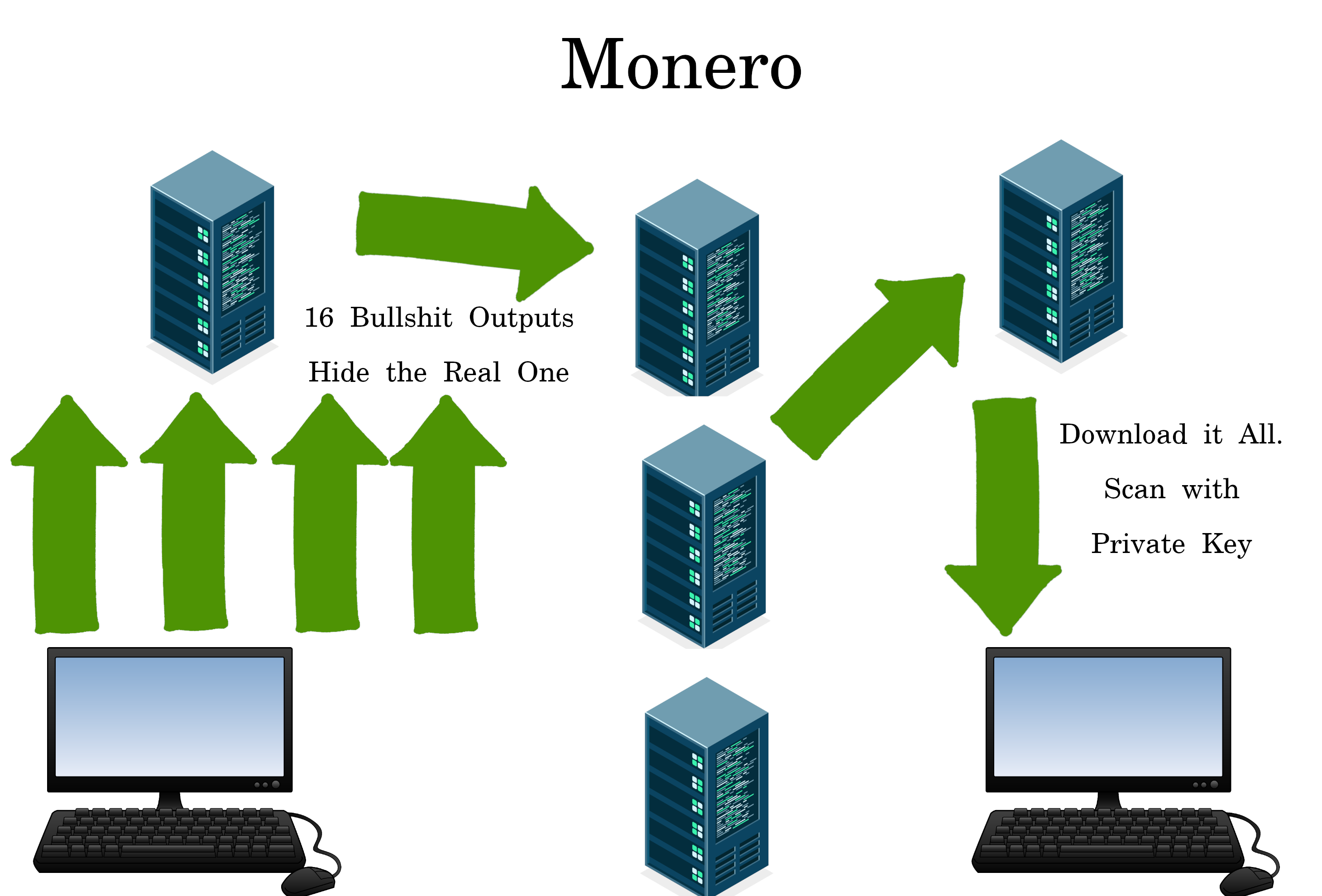
Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables
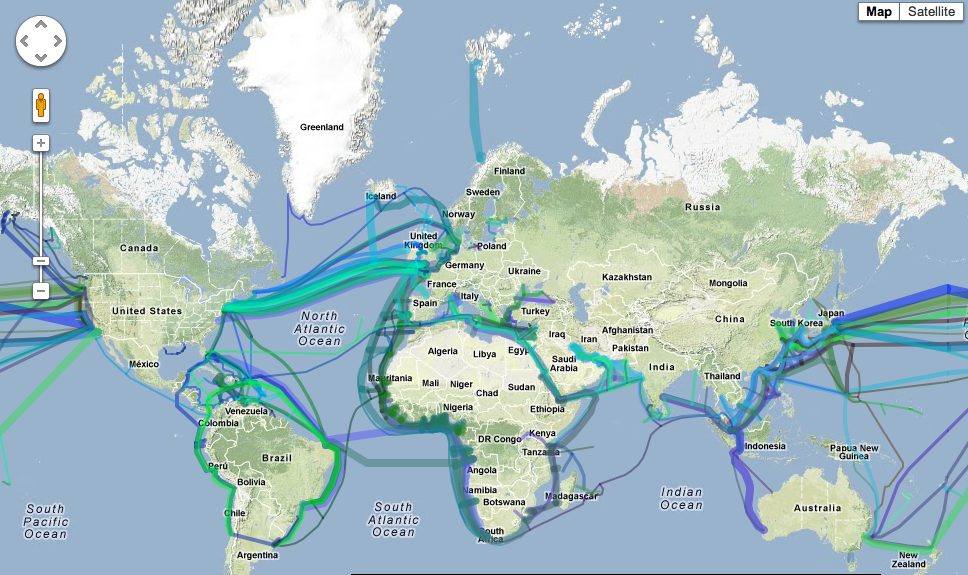

Simplified Privacy
Our VPN allows for split traffic with fake decoy outputs, (like the “Monero of VPNs”). So your home ISP and the ocean cables see different packet sizes.
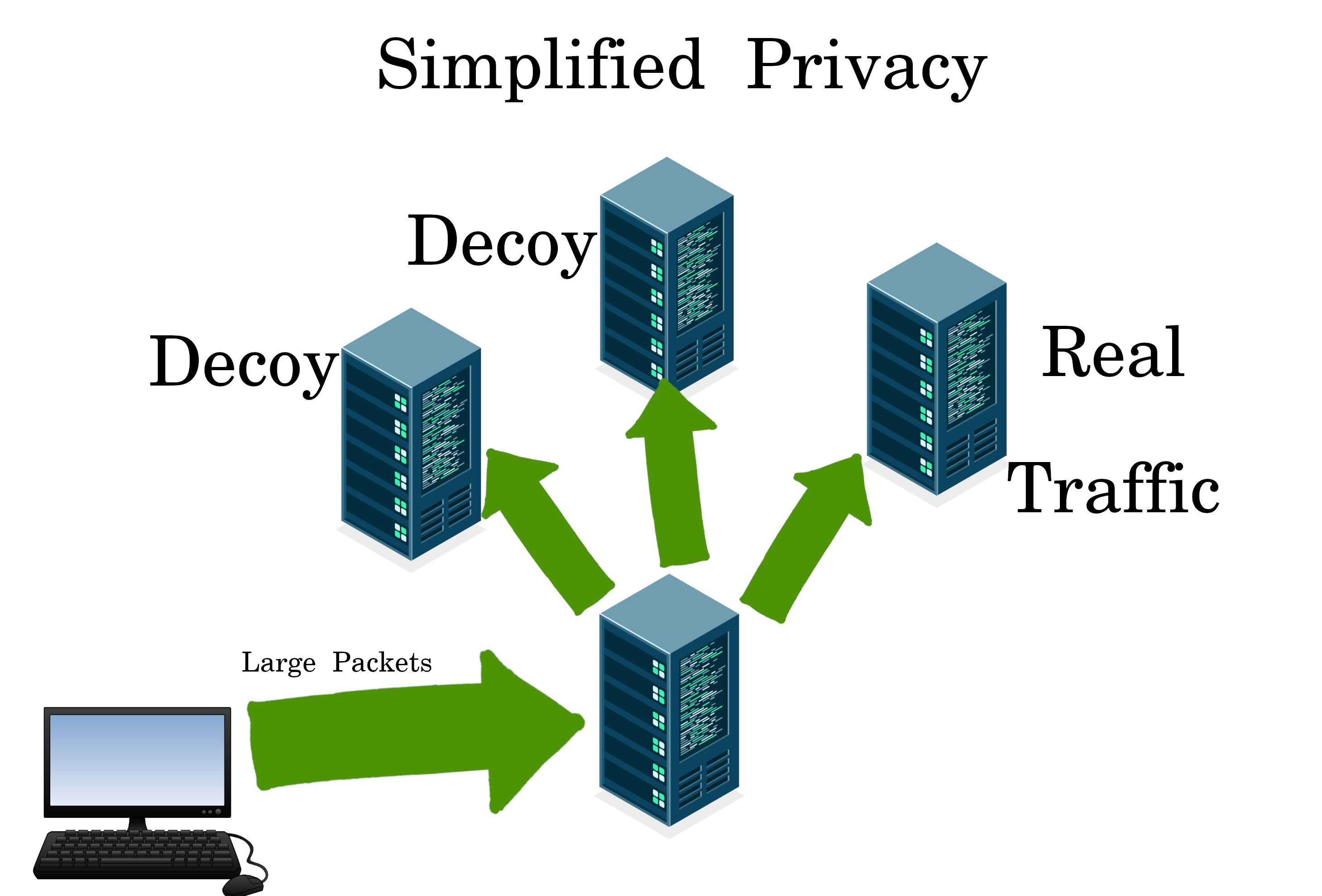
Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach: https://simplifiedprivacy.com/nsa-taps-ocean-cables/so-we-have-a-two-layer-split-traffic-approach.html
Get one easy to understand Picture for each protocol:

Signal
Signal is on the CIA contractor Amazon, and tries to use “sealed sender” to hide the metadata. However it’s flawed.

Learn Tips for Signal: https://simplifiedprivacy.com/signal/index.html
~~
XMPP
XMPP is well-trusted, but the OMEMO encryption dies with the domain it’s linked to. This means XMPP is nothing more than end-to-end encrypted email (with rotating keys).

Learn about XMPP here: https://video.simplifiedprivacy.com/xmpp/
~~
SimpleX
SimpleX splits up messages into a give and take. It’s similar to a double-federated model.

SimpleX users can change the relays mid-conversation, but new incoming messages are tied to government domains that can be censored.
~~
Session
Session transcends physical locations through unique DNS, onion-routing, and data stored in a BitTorrent database.

We use Session for an uncensored email list: https://simplifiedprivacy.com/uncensored/index.html
~~
Arweave
Arweave is to websites, what Session is to messages. Both have nodes being paid in a crypto to host a BitTorrent database. The main difference is Arweave stores the data DIRECTLY ON the blockchain.. and potentially forever.

Learn about Arweave here: https://simplifiedprivacy.com/arweave/Arweave-QA/index.html
~~
Nostr
Nostr has no blockchain. Users cryptographically sign messages, and then directly post and receive from relays.

Learn about Nostr here: https://video.simplifiedprivacy.com/nostrtutorial
~~
Bastyon
Bastyon is the “Russian Nostr” because it’s good at penetrating Firewalls. Unlike Nostr, Bastyon has a blockchain, and home client computers can directly and easily act as nodes (which makes it tough for governments to block).

Learn about Bastyon here: https://simplifiedprivacy.com/bastyon-works/how.html
~~
Bitcoin Lightning
Lightning Channels are like an Abacus, keeping track of who owes who on the Layer 1. It does multiple hops for privacy, similar to Tor.

~~
Monero
Monero hides the data by having fake “decoy” signers. Then having the reciever download and scan all the transactions for a match.

Learn about Monero here: https://video.simplifiedprivacy.com/how-xmr-works/
~~
The NSA Taps the Ocean Cables


Simplified Privacy
Our VPN allows for split traffic with fake decoy outputs, (like the “Monero of VPNs”). So your home ISP and the ocean cables see different packet sizes.

Proof of Concept Beta
The VPN currently supports split-traffic, but the cover traffic is manual. For example, opening a 2nd profile with a 12-hour music list, which is very easy with a bookmark homepage. One advantage of manual, is the server doesn’t know if it’s cover traffic or not. But we will be automating the cover traffic in future beta rounds.
Learn About Our Split Approach: https://simplifiedprivacy.com/nsa-taps-ocean-cables/so-we-have-a-two-layer-split-traffic-approach.html
