Gammitin (Ben) 💾 on Nostr: So I've disassembled the binary in a reverse engineering tool and I'm starting to ...
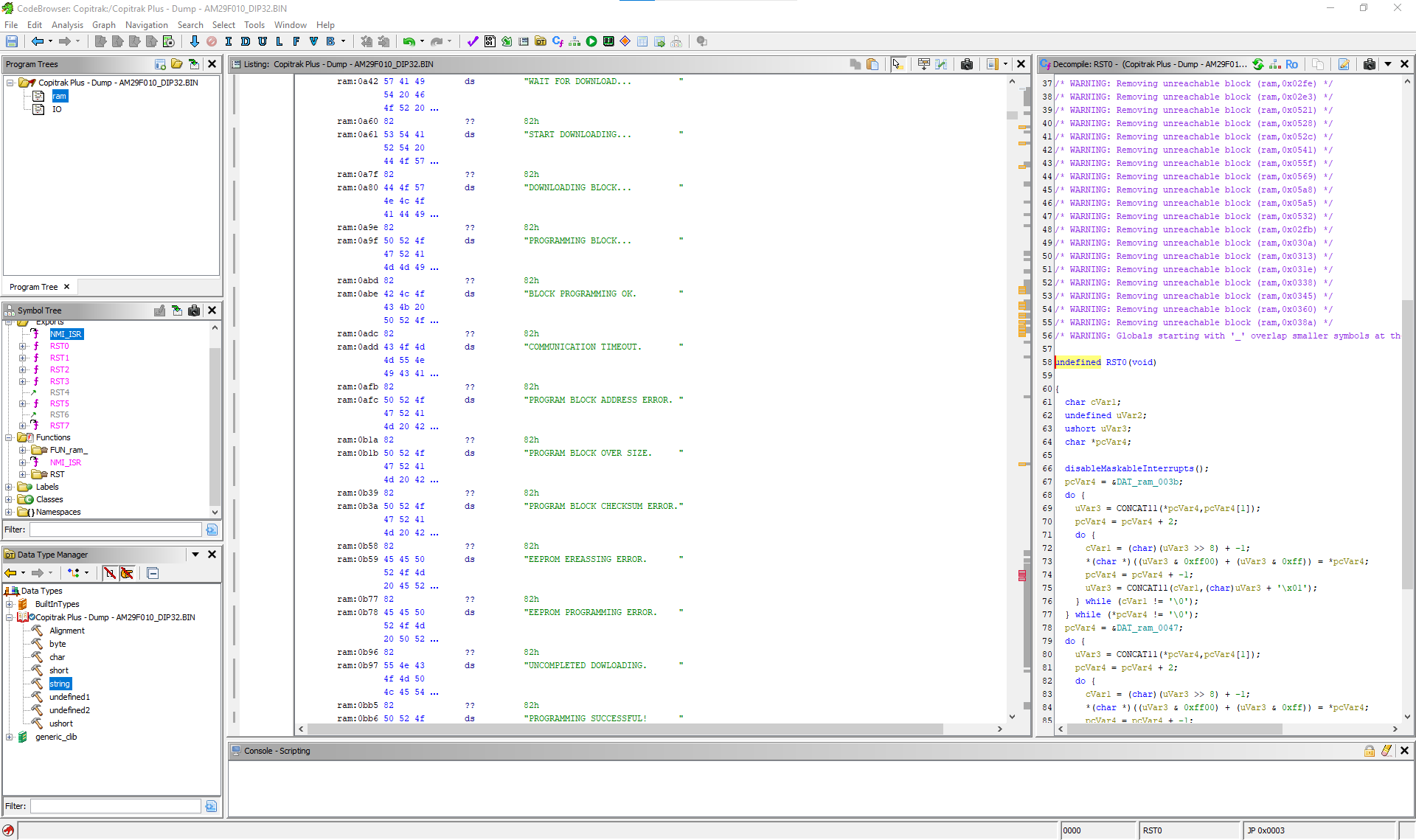
So I've disassembled the binary in a reverse engineering tool and I'm starting to look through to see if I can find anything interesting.
I did find out that when it boots, it tries to download a file from the server and then programs the flash if it downloads successfully:
Published at
2024-11-14 20:55:27Event JSON
{
"id": "7347702f7b123f26027209e13ba6fae4040b4b39593f4a7e44c3a3ef740a6bac",
"pubkey": "10eaa37d556287124ec26d6d217260483bc8b1a82decd844685ff274b11e668d",
"created_at": 1731617727,
"kind": 1,
"tags": [
[
"e",
"2f1613f83f6b35f52f1aed214bdff297969796874a562dfe7ca6f798a92a6e40",
"wss://relay.mostr.pub",
"reply"
],
[
"imeta",
"url https://files.mastodon.social/media_attachments/files/113/483/299/260/046/963/original/0ae42a34a2b16c55.png",
"m image/png",
"dim 1920x1139",
"blurhash U7R{#[gH8{%2^-kjM}oe00oyx[tR.6MyNFRj"
],
[
"proxy",
"https://mastodon.social/users/Gammitin/statuses/113483299358178370",
"activitypub"
]
],
"content": "So I've disassembled the binary in a reverse engineering tool and I'm starting to look through to see if I can find anything interesting.\nI did find out that when it boots, it tries to download a file from the server and then programs the flash if it downloads successfully:\n\nhttps://files.mastodon.social/media_attachments/files/113/483/299/260/046/963/original/0ae42a34a2b16c55.png",
"sig": "a56d453db4914e25dfeaac5dd24c7c36c879f990f44d84e4467463678daae087e460ea1611ef0ab645696b11649a2f0c7e1565e5bb3f88f20b54acf15ab38027"
}

